Blog
Read the latest blogs
Security configurations in ServiceNow cause QA teams a lot of headaches every time new system versions are released. One way to thoroughly test these configurations is to use impersonation as part of the test automation.
The ServiceNow platform can be configured to allow different user roles access to different features and items. When new versions of ServiceNow are applied, custom security configurations are at risk of creating bugs and unwanted side effects. Often, testing security configurations take lower priority to other functional testing.
This can cause security issues as well as bad user experiences. For example, a user might be able to see a button, but not push it, or a user might be able to approve own requests.
An efficient way of testing security configurations is to rely on user impersonation as part of your test automation. This is best done by using a reusable component, or sub-flow, across test cases.
At LEAPWORK, we've made a bunch of pre-made, out-of-the-box samples, or sub-flows, specifically for ServiceNow automation.
Instructions: Download and install the ServiceNow sample flows.
The samples include a sub-flow for impersonating users in ServiceNow, called "SNC Impersonate".
This way, a single automation flow can be used to both take care of the functional testing of a process and to verify the security configuration of that process.
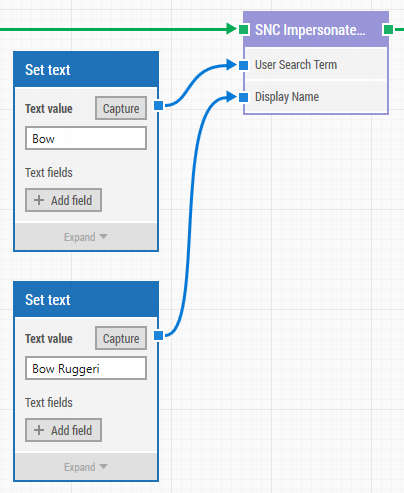
The SNC Impersonate component is typically used after a login and other processes have been executed. For example, whenever a change request has been submitted, the approval of this request can be tested by impersonating as a user with the right privileges. In this case, the Impersonate component is then used to automate the switch between the "requester" role and the "approver" role. Again, the same automation flow takes care of testing both functionality and security configurations.
Another scenario could be to impersonate as a user that shouldn't have access to view a Change Request and then verify that this is the case.
As demonstrated in the video tutorial, to execute a user impersonation with the LEAPWORK Impersonate component, you simply search for the user you want to impersonate and then specify the display name to use in verifying that the impersonation was successful.
Check out LEAPWORK's tutorials, out-of-the-box samples, and educational resourcesto get started with ServiceNow automation.
©2024, Leapwork. All rights reserved.